第八届强网杯WriteUp_2024
大约 5 分钟
Misc
谍影重重5.0
题目内容:
我国某部门已经连续三年对间谍张纪星进行秘密监控,最近其网络流量突然出现大量的神秘数据,为防止其向境外传送我国机密数据,我们已将其流量保存,请你协助我们分析其传输的秘密信息。 附件
通过流量分析,发现很多msb2加密数据,应该是需要构造解密密钥。通过文章
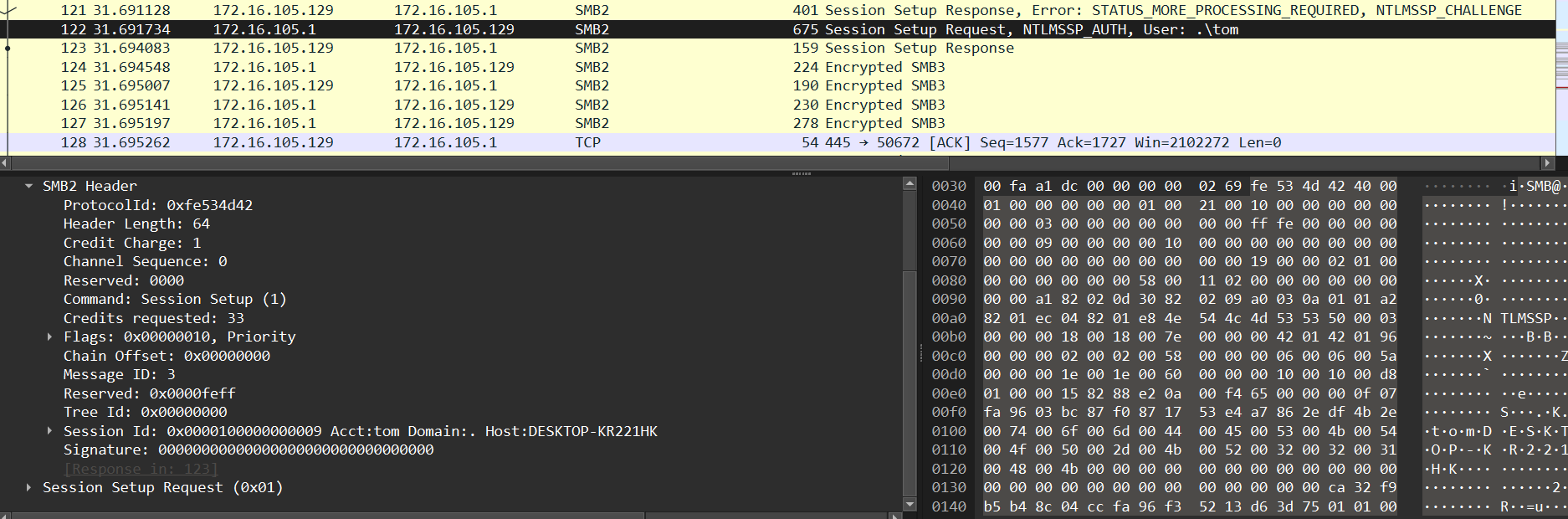
在 .pcap 中,您可以看到有人连接到 SMB 共享并使用 NTLMv2 身份验证。暗示使用了弱身份验证。因此,我提取了哈希值并构建了以下哈希值:
构造方法:
username::domain:NTLM Service Challenge:NTProofStr:不包含ntproofstr的ntlmv2_response值
=> hashcat格式最终是这样的
tom::.::c1dec53240124487::ca32f9b5b48c04ccfa96f35213d63d75::010100000000000040d0731fb92adb01221434d6e24970170000000002001e004400450053004b0054004f0050002d004a0030004500450039004d00520001001e004400450053004b0054004f0050002d004a0030004500450039004d00520004001e004400450053004b0054004f0050002d004a0030004500450039004d00520003001e004400450053004b0054004f0050002d004a0030004500450039004d0052000700080040d0731fb92adb0106000400020000000800300030000000000000000100000000200000bd69d88e01f6425e6c1d7f796d55f11bd4bdcb27c845c6ebfac35b8a3acc42c20a001000000000000000000000000000000000000900260063006900660073002f003100370032002e00310036002e003100300035002e003100320039000000000000000000
hashcat/john 爆密码获取密钥
构造完成后
hashcat -m <hash_type> -a <attack_mode> <hash_file> <wordlist_file>
hashcat -m 5600 -a 0 hash.txt rockyou.txt
john --format=netntlmv2 crackme.txt --wordlist=rockyou.txt
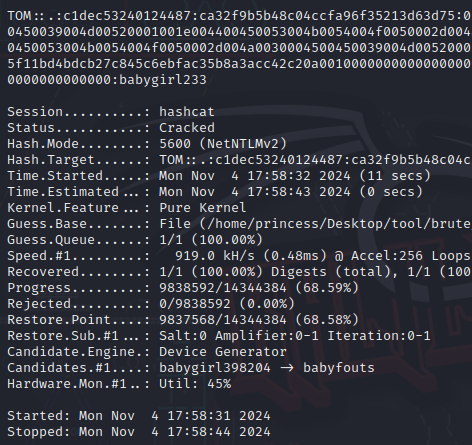
爆出密码:babygirl233
=> 整理一下我们知道的信息
user: tom
domain: .
password: babygirl233
ntproofstr: ca32f9b5b48c04ccfa96f35213d63d75
Session Key: 5643a37f253b00b2f52df1afd48c1514
Session Id: 0x0000100000000009
=> 用脚本计算密钥
import hashlib
import hmac
import binascii
from Cryptodome.Cipher import ARC4
from Cryptodome.Hash import MD4 # 使用pycryptodome中的MD4
def md4_hash(password):
"""Calculate the MD4 hash of the given password."""
hash_obj = MD4.new()
hash_obj.update(password.encode('utf-16le'))
return hash_obj.digest()
def calculate_response_nt_key(username, domain, password):
"""Calculate the Response NT Key."""
user = username.upper().encode('utf-16le')
domain = domain.upper().encode('utf-16le')
password_hash = md4_hash(password)
# HMAC-MD5
h = hmac.new(password_hash, digestmod=hashlib.md5)
h.update(user + domain)
return h.digest()
def generate_encrypted_session_key(key_exchange_key, encrypted_session_key):
"""Decrypt the encrypted session key using the key exchange key."""
cipher = ARC4.new(key_exchange_key)
return cipher.encrypt(encrypted_session_key)
def main():
username = "tom"
password = "babygirl233"
domain = "." # Use appropriate domain if available
nt_proof_str = "ca32f9b5b48c04ccfa96f35213d63d75" # Example NTProofStr
encrypted_session_key_hex = "5643a37f253b00b2f52df1afd48c1514" # Example encrypted session key
# Convert hex string to bytes
encrypted_session_key = binascii.unhexlify(encrypted_session_key_hex)
# Calculate Response NT Key
response_nt_key = calculate_response_nt_key(username, domain, password)
# Calculate Key Exchange Key
nt_proof_str_bytes = binascii.unhexlify(nt_proof_str)
key_exchange_key = hmac.new(response_nt_key, digestmod=hashlib.md5)
key_exchange_key.update(nt_proof_str_bytes)
key_exchange_key = key_exchange_key.digest()
# Decrypt the session key
session_key = generate_encrypted_session_key(key_exchange_key, encrypted_session_key)
print("Decrypted Session Key:", binascii.hexlify(session_key).decode())
if __name__ == "__main__":
main()
得到Decrypted Session Key: a3abe4d64394909a641062342ffe291b
在 Wireshark 中配置解密
Edit(编辑) > Preferences(首选项)> Protocols(协议) > SMB2
- "Enable decryption"(启用解密)
- 在 "Decryption keys"(解密密钥) 栏中,输入会话密钥,格式为:
session_key:<session_id>:<session_key>。
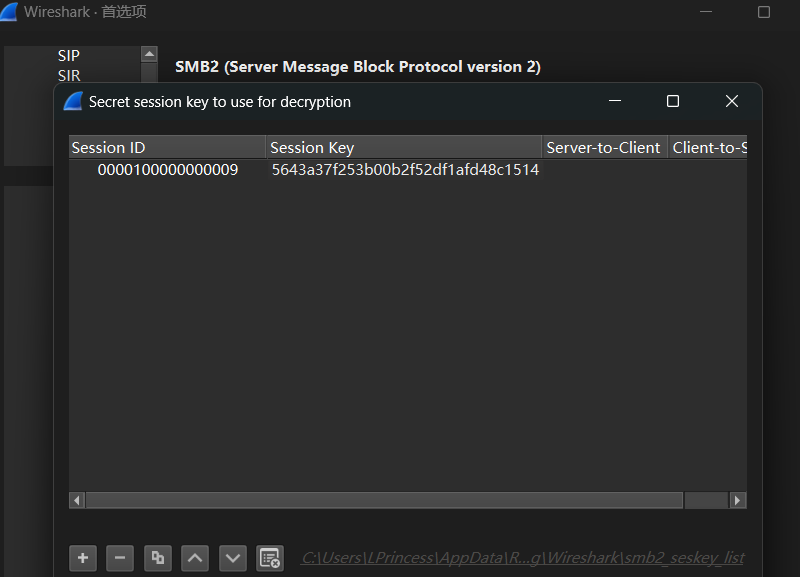
这里有一个坑
这里的session_id会以不同的字节顺序显示
字节序(Endianness) Session ID 的表示涉及字节序问题。计算机中的数据可以使用不同的字节序表示,主要有两种:
- 大端字节序(Big Endian):高位字节在前,低位字节在后。
- 小端字节序(Little Endian):低位字节在前,高位字节在后。
因此这题Session ID前面尝试0000000010000009无效,因此判断可能是0900000000100000
=> 导出解密文件:
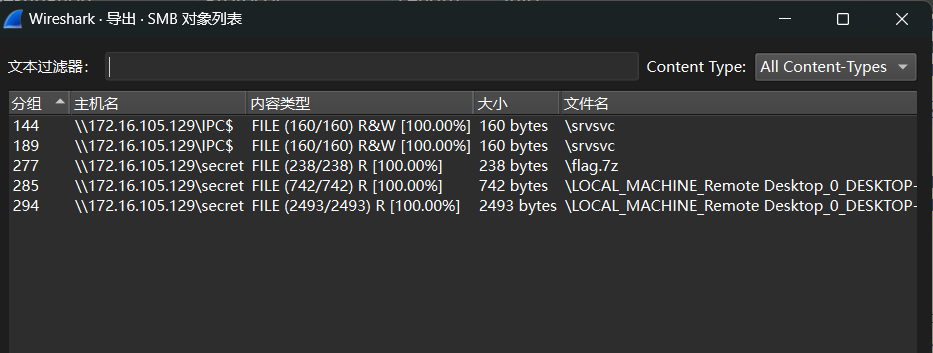
导出有flag.7z —— 被加密,还有rdp,tls,先把证书导入进去
wireshark的tls证书支持的是.pem格式,用openssl转换
猜测密码:mimikatz
提取.pem私钥
openssl pkcs12 -in file.pfx -nokeys -out cert.pem
键盘码:
def map_keycode(key_code):
"""根据扫描码返回相应的字符或描述"""
# 特殊键的映射
special_keys = {
0x00: 'None', # No key
0x01: 'Esc', # Esc
0x02: '1', # 1
0x03: '2', # 2
0x04: '3', # 3
0x05: '4', # 4
0x06: '5', # 5
0x07: '6', # 6
0x08: '7', # 7
0x09: '8', # 8
0x0A: '9', # 9
0x0B: '0', # 0
0x0C: '-', # -
0x0D: '=', # =
0x0E: 'Backspace', # Backspace
0x0F: 'Tab', # Tab
0x10: 'Q', # Q
0x11: 'W', # W
0x12: 'E', # E
0x13: 'R', # R
0x14: 'T', # T
0x15: 'Y', # Y
0x16: 'U', # U
0x17: 'I', # I
0x18: 'O', # O
0x19: 'P', # P
0x1A: '[', # [
0x1B: ']', # ]
0x1C: 'Enter', # Enter
0x1D: 'Left Ctrl', # Left Control
0x1E: 'A', # A
0x1F: 'S', # S
0x20: 'D', # D
0x21: 'F', # F
0x22: 'G', # G
0x23: 'H', # H
0x24: 'J', # J
0x25: 'K', # K
0x26: 'L', # L
0x27: ';', # ;
0x28: "'", # '
0x29: 'Grave', # `
0x2A: 'Left Shift', # Left Shift
0x2B: 'Backslash', # \
0x2C: 'Z', # Z
0x2D: 'X', # X
0x2E: 'C', # C
0x2F: 'V', # V
0x30: 'B', # B
0x31: 'N', # N
0x32: 'M', # M
0x33: ',', # ,
0x34: '.', # .
0x35: '/', # /
0x36: 'Right Shift', # Right Shift
0x37: 'Keypad *', # Keypad *
0x38: 'Alt', # Alt
0x39: 'Space', # Space
0x3A: 'Caps Lock', # Caps Lock
0x3B: 'F1', # F1
0x3C: 'F2', # F2
0x3D: 'F3', # F3
0x3E: 'F4', # F4
0x3F: 'F5', # F5
0x40: 'F6', # F6
0x41: 'F7', # F7
0x42: 'F8', # F8
0x43: 'F9', # F9
0x44: 'F10', # F10
0x45: 'F11', # F11
0x46: 'F12', # F12
0x47: 'Num Lock', # Num Lock
0x48: 'Keypad 7', # Keypad 7
0x49: 'Keypad 8', # Keypad 8
0x4A: 'Keypad 9', # Keypad 9
0x4B: 'Keypad -', # Keypad -
0x4C: 'Keypad 4', # Keypad 4
0x4D: 'Keypad 5', # Keypad 5
0x4E: 'Keypad 6', # Keypad 6
0x4F: 'Keypad +', # Keypad +
0x50: 'Keypad 1', # Keypad 1
0x51: 'Keypad 2', # Keypad 2
0x52: 'Keypad 3', # Keypad 3
0x53: 'Keypad 0', # Keypad 0
0x54: 'Keypad .', # Keypad .
0x5B: 'Left Win', # Left Windows
0x5C: 'Right Win', # Right Windows
0x5D: 'Menu', # Menu
0x5E: 'Right Ctrl', # Right Control
0x5F: 'Right Alt', # Right Alt
}
return special_keys.get(key_code, f"Unknown key code: {key_code}")
def process_keyboard_data(data):
"""处理键盘输入数据,返回对应的按键描述"""
output = []
for entry in data:
# 分割扫描码并转换为整数
key_codes = entry.split(',')
mapped_keys = [map_keycode(int(code, 16)) for code in key_codes]
output.append(' '.join(mapped_keys))
return output
# 示例键盘输入数据
keyboard_data = [
"0x0f,0x2a,0x36,0x1d,0x1d,0x0f,0x38,0x0f,0x38,0x0f",
"0x0f,0x2a,0x36,0x1d,0x1d,0x0f,0x38,0x0f,0x38,0x0f",
"0x0f,0x5b,0x5c,0x2a,0x36,0x1d,0x1d,0x0f,0x38,0x0f,0x38,0x0f",
"0x14",
"0x23",
"0x12",
"0x2a",
"0x39",
"0x08",
"0x2c",
"0x39",
"0x19",
"0x1e",
"0x1f",
"0x1f",
"0x11",
"0x18",
"0x13",
"0x20",
"0x39",
"0x17",
"0x1f",
"0x39",
"0x21",
"0x28",
"0x1a",
"0x2a",
"0x11",
"0x17",
"0x31",
"0x20",
"0x18",
"0x11",
"0x1f",
"0x0c",
"0x2a",
"0x19",
"0x1e",
"0x1f",
"0x1f",
"0x11",
"0x18",
"0x13",
"0x20",
"0x1b",
"0x2a",
"0x0a",
"0x04",
"0x05",
"0x08",
"0x0b",
"0x02",
"0x04",
"0x02",
"0x09",
"0x03",
"0x28",
"0x1f",
"0x1d",
"0x0f,0x2a,0x36,0x1d,0x1d,0x0f,0x38,0x0f,0x38,0x0f"
]
# 处理每行数据
keyboard_output = process_keyboard_data(keyboard_data)
# 将结果写入文本文件
with open('keyboard_output.txt', 'w') as file:
for entry in keyboard_output:
file.write(entry + '\n')
print("finished_keyboard_output.txt")
keyboard_output:
Tab Left Shift Right Shift Left Ctrl Left Ctrl Tab Alt Tab Alt Tab
Tab Left Shift Right Shift Left Ctrl Left Ctrl Tab Alt Tab Alt Tab
Tab Left Win Right Win Left Shift Right Shift Left Ctrl Left Ctrl Tab Alt Tab Alt Tab
T
H
E
Left Shift
Space
7
Z
Space
P
A
S
S
W
O
R
D
Space
I
S
Space
F
'
[
Left Shift
W
I
N
D
O
W
S
-
Left Shift
P
A
S
S
W
O
R
D
]
Left Shift
9
3
4
7
0
1
3
1
8
2
'
S
Left Ctrl
Tab Left Shift Right Shift Left Ctrl Left Ctrl Tab Alt Tab Alt Tab
flag.7z密码就是babygirl2339347013182